As hostile nation-state actors turn to cyber-attacks, they are becoming more strategic. Strategic attacks are those in which an attacker, often a hostile nation-state actor, penetrates a network to gain control of a process, adjusting valves and moving set-points. These attacks are far costlier and more dangerous than blunt-force attacks that lead to a shutdown, and their costs could potentially be counted in human lives. One such attack, for instance, introduced a toxic chemical into a community’s water supply in Florida. Though this attack was discovered and stopped, it is an indication of things to come. The financial loss of such attacks could easily be measured in billions of dollars, but that pales in comparison with the potential loss of lives.
Some of the hardest to detect cyber-attacks are wireless; including man-in-the-middle attacks and rogue access points. To address this, Endpoint is introducing a Wireless Intrusion Detection System (WIDS) based on an amazing new technology which sees a naturally occurring fingerprint in every wireless signal. It uses the polarization of a signal as a unique and stable identifier.
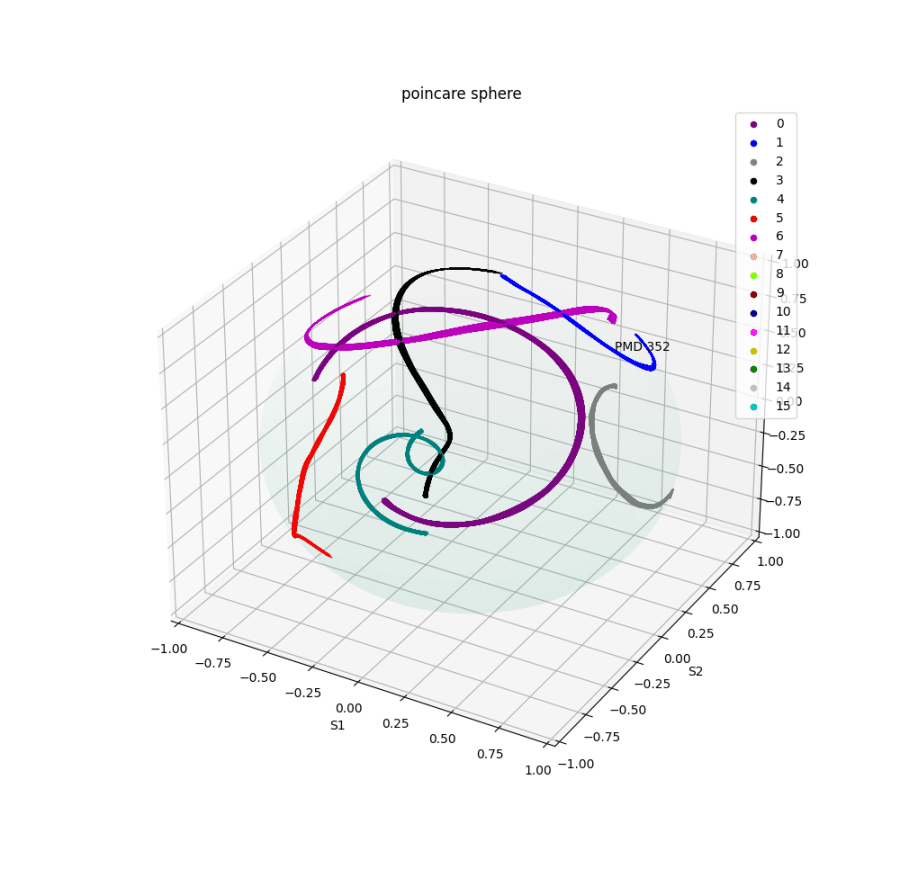
A discovery has been made at the University of Notre Dame under the direction of researcher Dr. Thomas Pratt. Dr. Pratt discovered that polarization mode dispersion not only affects optical signals, but also RF signals and that such dispersion is a continuous function of frequency. This fact has been characterized in a laboratory environment under controlled conditions using 802.11n standard Wi-Fi signals. The results are astounding, in that each RF signal seems to have a completely unique fingerprint in its dispersion characteristics.
When plotted on a Poincaré sphere, the fingerprint of a broadband Wi-Fi signal takes the form of a continuous curve. It is important to note that the points on the curve correspond to various frequencies in the transmission, but are not related to the signal strength. The discovery that these functions take a continuous form is surprising and formed the basis of Endpoint's WIDS that can be innovated to provide secure wireless transmission. These fingerprints provide a natural authentication of fixed, wireless endpoint devices. A WIDS can detect a wireless intruder and notify a network administrator in a factory or refinery. This breakthrough innovation provides authentication in the physical layer, not requiring any demodulation of signal and thus making it widely compatible with various protocols and devices.
Now, network administrators can actually prevent wireless cyber-attacks, not simply respond to them.
Video
Voting
-
ABOUT THE ENTRANT
- Name:Page Heller
- Type of entry:individual
- Profession:
- Number of times previously entering contest:2
- Page is inspired by:Cyber-attacks are now a danger to citizens as hackers attempt to poison our water supplies. It is time to get out in front of the hackers and prevent them from connecting to our networks. It is time to become proactive rather than remaining reactive. I want to seal off some of the hardest to detect attacks, those which use an IoT device to gain access to the network. My colleagues and I have now developed such a tool.
- Software used for this entry:Python, C++
- Patent status:patented