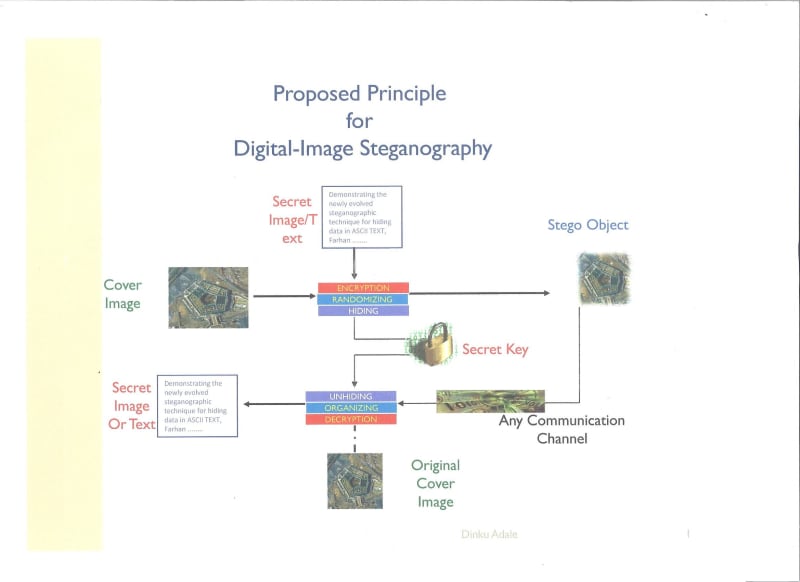
Steganography, derived from Greek, roughly translated as “cover writing.” It is a “hide and seek” system that embeds hidden information in unremarkable cover media so as not to arouse an eavesdropper’s suspicion except the intended recipient. Embedding a message into an image requires two files. The first is the innocent-looking image that will hold the hidden information, called the cover image. The second file is the message—the information to be hidden. The hiding system needs a host file, a prepared message file, and an optional key to insert the message into the host for creating a cover host. The seek system operates in reverse. To extract the hidden message it takes a covert host and an optional key as input. Steganography plays the central role in secret message communication. Various images and video formats can be used as host as these files can hide huge amount of data without perceptible impact on the carriers. The extent of host covertness depends on the capabilities of the perceived threat. This entry focuses on the use of encryption in conjunction with randomization and cryptography for steganography and discusses the various methods of message concealment in digital images. This makes the attack almost impossible as the hidden data masquerades as random data throughout the image. Encryption is a way of encoding the data or putting the data through a cipher by using a key or password. Cryptography is the process of hiding data.
Like this entry?
-
About the Entrant
- Name:Dinku Adale
- Type of entry:individual
- Hardware used for this entry:video/audio imagesSoftware used for this entry:C++, encryption algorithm, video/audio data
- Patent status:none