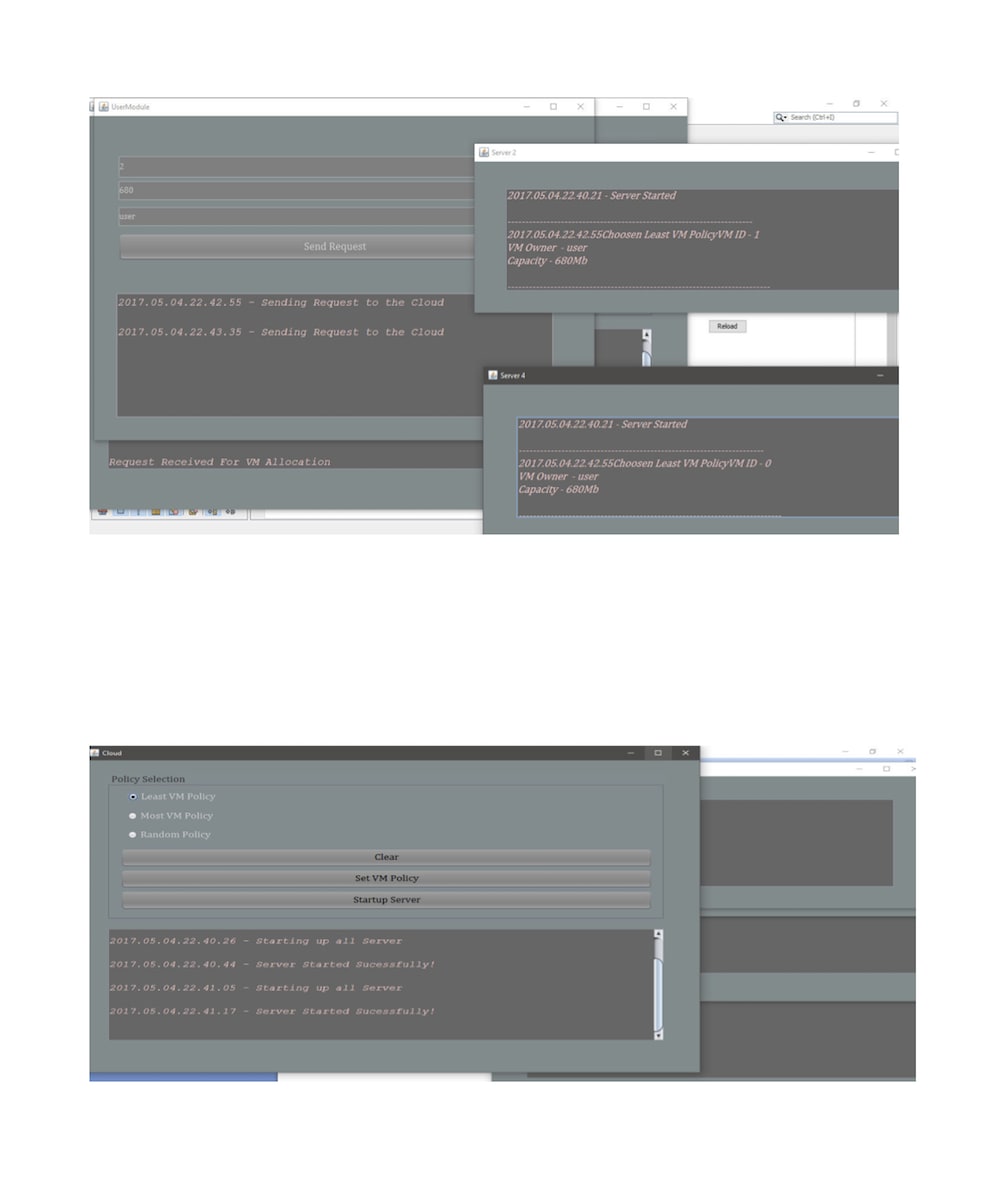
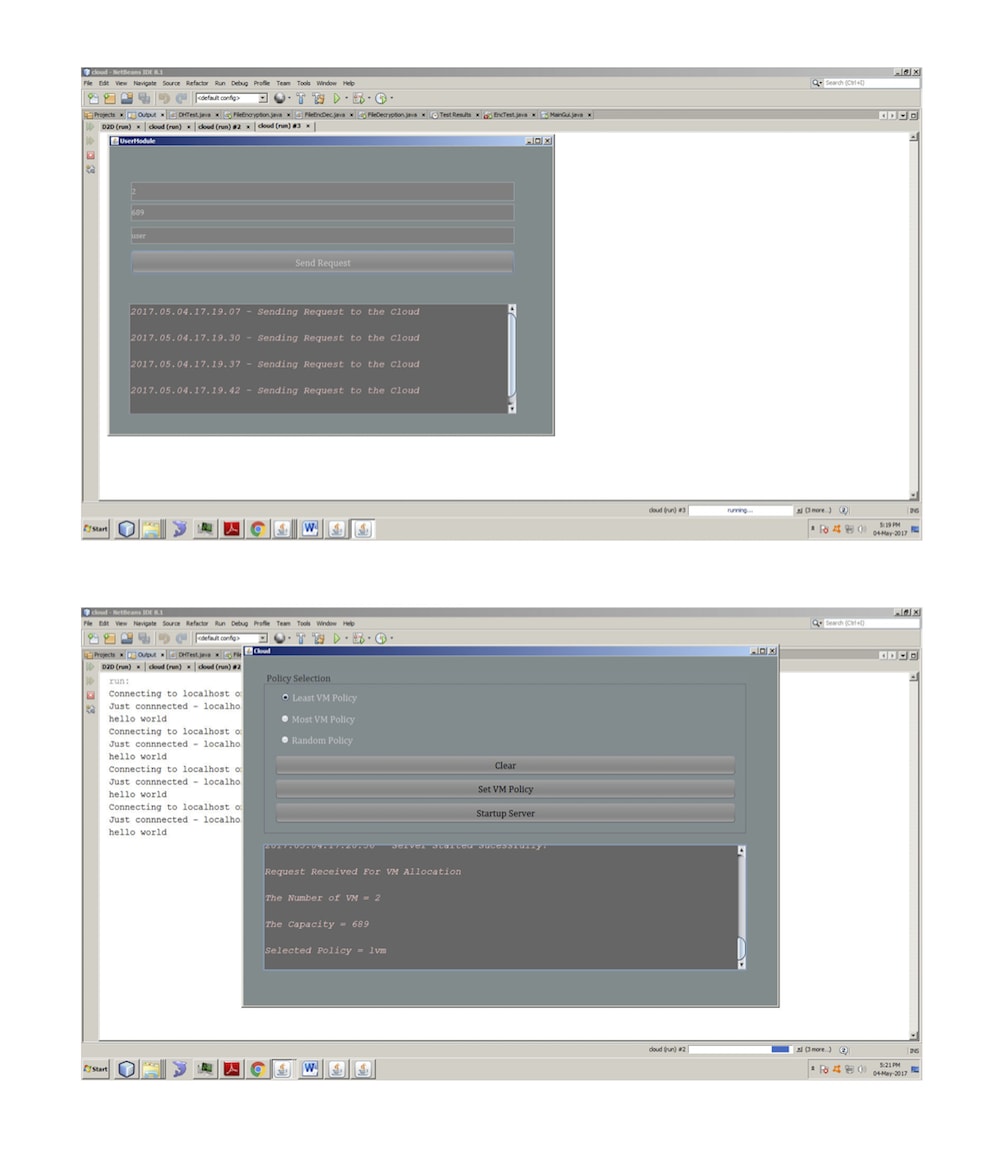
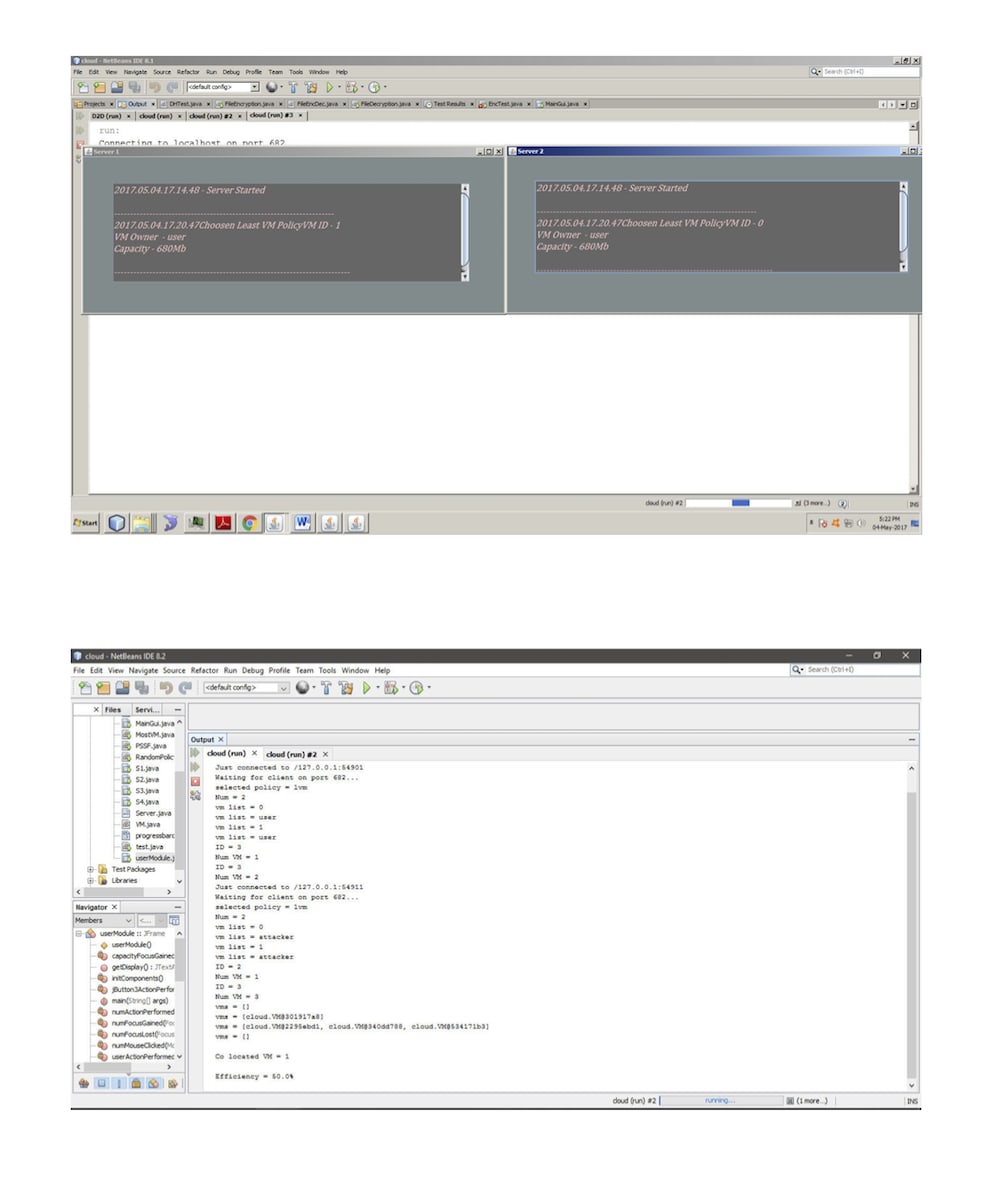
This PROJECT reviews and provides clarification to the meaning and concept of cloud computing with particular reference to Infrastructure as a Service (IaaS) and its underlying virtualization technologies. A review of virtualization technologies and approaches is presented with key vulnerabilities to security threats and mitigation strategies and countermeasures are also presented. This knowledge is imperative in making virtual Information Technology (IT) environment more secure and robust and can help improve the operational efficiency of Virtual Machines (VMs)in such a manner that organizations can benefit from virtualization technology in particular and the cloud computing systems in general. Cloud computing improves utilization and flexibility of allocating computing resources while reducing the infrastructural costs. However, customers can face new security risks when they use cloud computing platforms. In this paper, we focus on one such threat − the co-resident attack, where malicious users build side channels and extract private information from virtual machines co-located on the same server.Specifically, we (1) define security metrics for assessing the attack; (2) model these metrics, and compare the difficulty of achieving co-residence under three commonly used policies; (3) design a new policy that not only mitigates the threat of attack, but also satisfies the requirements for workload balance and low power consumption; and (4) implement, test, and prove the effectiveness of the policy.A straightforward solution to this attack is to eliminate the side channels. However, most of these methods are not suitable for immediate deployment due to the required modifications to current cloud platforms. In my work, we approach this problem from a completely different perspective. Before the attacker is able to extract any private information from the victim, they first need to co-locate their VMs with the target VMs. It has been shown that the attacker can achieve an efficiency rate of as high as 40%,, which means 4 out of 10 attacker’s VMs can co-locate with the target. This motivates to study how to effectively minimise this value. From a cloud provider’s point of view, the VM allocation policy (also known as VM placement − we use these two terms interchangeably in this paper) is the most important and direct control that can be used to influence the probability of co-location. Consequently, we aim to design a secure policy that can substantially increase the difficulty for attackers to achieve co-residence.our contributions include: (1) we define secure metrics that measure the safety of a VM allocation policy, in terms of its ability to defend against co-resident attacks; (2) we model these metrics under three basic but commonly used VM allocation policies, and conduct extensive experiments on the widely used simulation platform CloudSim to validate the models; (3) we propose a new secure policy, which not only significantly decreases the probability of attackers co-locating with their targets, but also satisfies the constraints in workload balance and power consumption; and (4) we implement and verify the effectiveness of our new policy using the popular open-source cloud software.In future we can try to minimize the attack on multiple systems.
Like this entry?
-
About the Entrant
- Name:Kajol Chaurasia
- Type of entry:teamTeam members:PUJA SENGUPTA KEVIN MATHEW
- Software used for this entry:NETBEANS
- Patent status:none