Power Fingerprinting (PFP) is a cyber security solution capable of directly detecting malicious intrusions in critical infrastructure and Industrial Control Systems (ICS). PFP allows the monitoring of platforms with limited computational resources and memory, often found in ICSs and Programmable Logic Controllers (PLCs), which would not have the resources to support a traditional security monitoring approaches, such as anti-virus.
A cyber attack to critical infrastructure can have devastating consequences to national security. Yet, solutions capable of monitoring the execution of ICSs are notoriously absent or deficient. Current cyber security solutions for ICSs focus on patching, peripheral defenses (firewalls, access control, air gaps), network monitoring, and signature-based detection on peripheral hosts (antivirus).
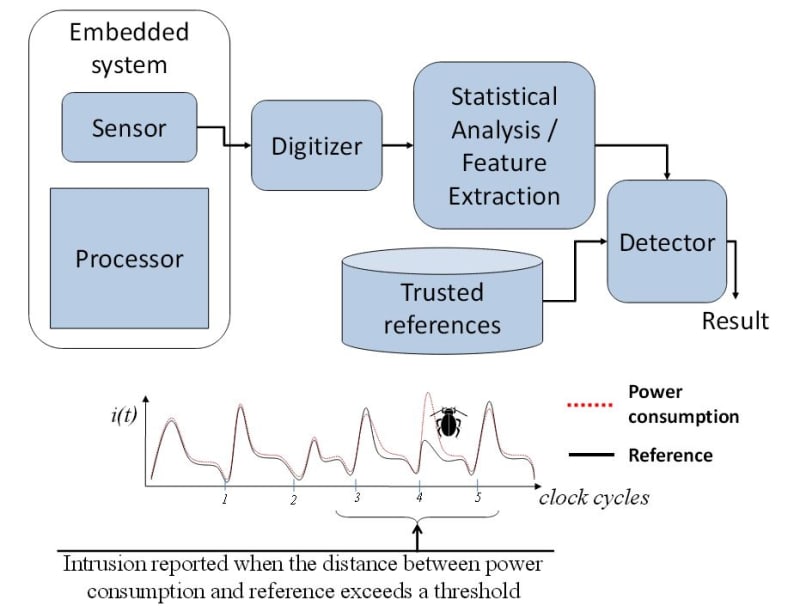
PFP follows a completely different approach for cyber security. It performs fine-grained anomaly detection on the processor’s power consumption to determine whether it has deviated from expected operation. A PFP monitor uses a physical sensor to capture fine-grained power consumption signals, also known as “side channels”, which contain tiny patterns or fingerprints that emerge during the transitions from one instruction to another. In PFP, power traces are processed using signal detection and classification techniques using an external device. The observed traces are compared against trusted references to assess whether the execution has deviated from its expected behavior, e.g. when an attack has managed to install malicious software. Because the actual monitoring is performed by an external device, the memory and processing overhead on the target systems is greatly reduced or totally eliminated. A PFP monitor can be assembled by integrating off-the-shelf components. The main element for commercialization involves the industrial extraction of trusted references, which can be performed by our clients with help from our tools and support.
PFP relies on sound signal detection and classification techniques that have been used for decades in the radar and communications fields. Using this approach, PFP delivers a quantitative measure of trust based on physical measurements and rigorous statistical analysis. PFP changes the asymmetry between defenders and cyber attackers. While malicious adversaries need to just find a single vulnerability, defenders need to address all potential vulnerabilities, resulting in a detection gap in modern antivirus systems. PFP helps balance this asymmetry because it does not need signatures from all malware. Furthermore, PFP is platform-agnostic, so it can work on all types of systems, even with legacy devices. More importantly, PFP is orthogonal to other security approaches, providing an extra layer of protection on top of traditional solutions.
The initial application for PFP is ICS monitoring because these systems are the highest-value targets that are also simple enough to easily characterize and monitor. A future application of the technology will be to monitor devices that compose the Internet of Things, simple devices addressable over the Internet, which is expected to emerge as major new technology over the next ten years. The market potential for PFP is huge, as cyber threats will remain. PFP provides an elegant solution to a rampant problem for which there is currently no alternative solution.
Video
-
Awards
-
 2013 Safety & Security Category Winner
2013 Safety & Security Category Winner -
 2013 Top 100 Entries
2013 Top 100 Entries
Like this entry?
-
About the Entrant
- Name:Carlos Aguayo Gonzalez
- Type of entry:teamTeam members:Carlos R. Aguayo Gonzalez, Power Fingerprinting, Inc.
Jeffrey H. Reed, Power Fingerprinting, Inc.
Steven Chen, Power Fingerprinting, Inc. - Patent status:pending